|
|
||
|---|---|---|
| MACsec_Utilitie | ||
| SFP_Flasher/v1.4 | ||
| resources | ||
| ReadMe.md | ||
| TC10_MACsec Demo.vs3 | ||
| TC10_MACsec Demo_1920x1080.vs3 | ||
ReadMe.md
MACsec and TC10 demo
Show case
The demo should show:
- MACsec secured datastream - only one Module is MACsec configured, modules might be swapped for showcasing
- TC10 controlled SFP plugs
Needed equipment:
- GigaStar
- 2 SFP: MV2221M 1000-Base-T1 modules, enabled for TC10/MACsec
1. Preparation
- If SFP module MV2221M 1000-Base-T1 is not yet flashed to support MACsec,
RGS_ICS_SFP_FLASHER_REV1_4.vs3 is needed to flash the module. Take care that also the binary sfp_mv2221m_b1_mchip.msgbin is available. - To download a MACsec configuration, actually you will need a small python script you find in the MACsec_Utilities folder (see 2.)
In this case you might have to install python onto the PC
Also you will need python_icspip instal python_icsandpip install pyyaml
2. Downloading MACsec configuration to SFP module
If the SFP module is ready for MACsec en- and decryption, you can download one of the Example YAML-Files
e.g.
programming SFP01 of device GS0728:
python test_sfp_macsec_util.py GS0728 --sfp --config_netid NETID_I2C2 --yaml test_sfp_macsec_Rule_wildcard_SecY_256_strip_noEncrypt_onlyCheck_sci_SA_sak0.yml
programming SFP02 of device GS0728: python test_sfp_macsec_util.py GS0728 --sfp --config_netid NETID_I2C3 --yaml test_sfp_macsec_Rule_wildcard_SecY_256_strip_noEncrypt_onlyCheck_sci_SA_sak0.yml
clearing SFP02 of device GS0728: python test_sfp_macsec_util.py GS0728 --sfp --config_netid NETID_I2C3 --yaml test_sfp_macsec_Rule_wildcard_SecY_256_strip_noEncrypt_onlyCheck_sci_SA_sak0.yml --reset
or just
python test_sfp_macsec_util.py GS0728 --sfp --config_netid NETID_I2C3 --reset
There are four example batch-files available to set and reset SFP01 and SFP02 modules. Device SN has to be adjusted.
3. Demosetup TC10_MACsec Demo.vs3
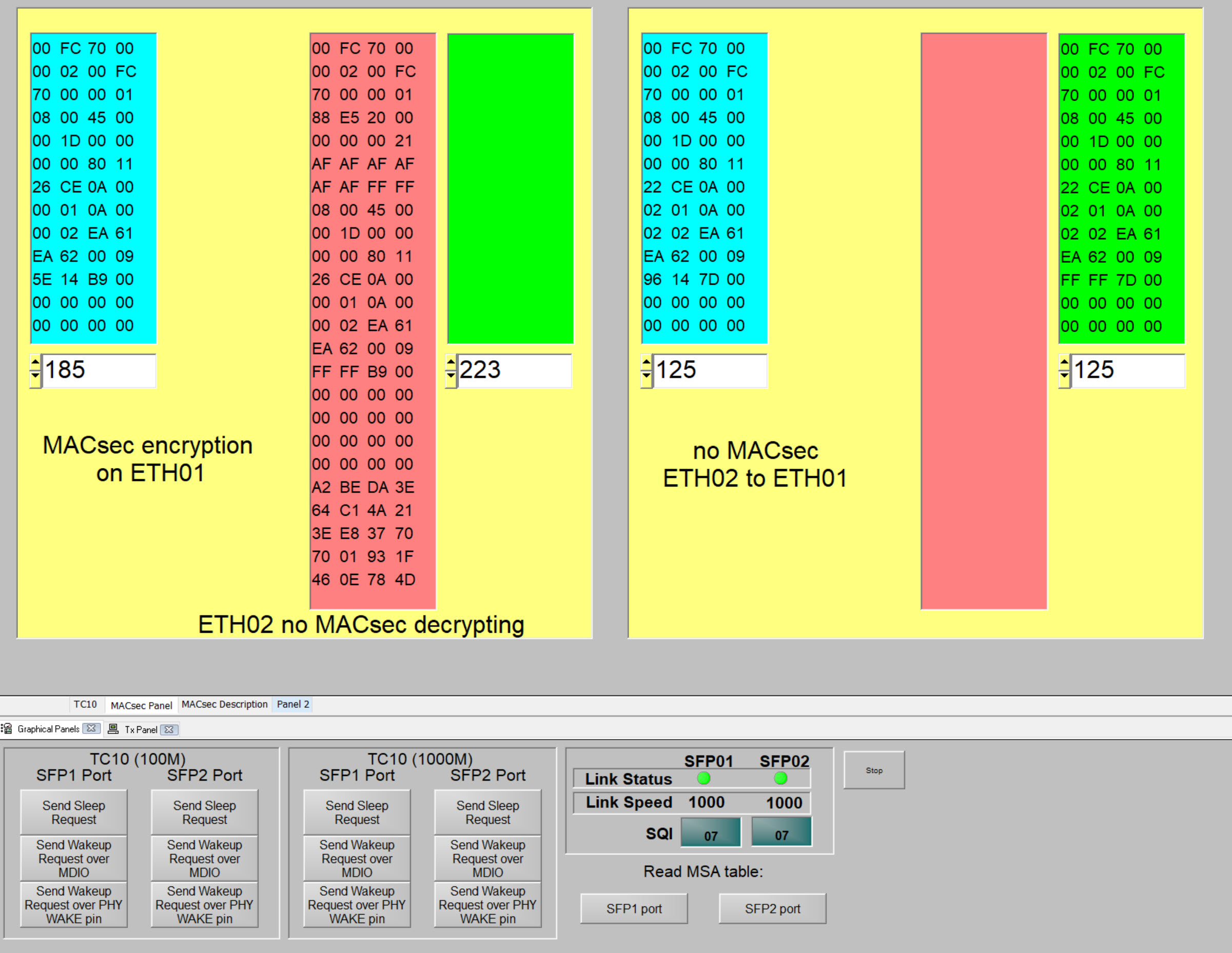 If SFP modules are swapped direction of encryption will change
If SFP modules are swapped direction of encryption will change